There has been a lot of noise or hype around the Internet of Things or IoT for the last couple of years. The volume of the chatter is actually still getting louder and has probably not reached its peak yet. It is supposed to impact everything, from how we do things at home, our traveling, shopping until the way manufacturers keep track of inventory. But what is IoT? How does it work? Is it really that important? How secure is it? And last but not least, how can you make a career in it?
What is the Internet of Things or IoT?
There are many different definitions and interpretations out there, which vary depending on whom you ask and the context. The interesting thing is that most of them are right, but at the same time confuse you even more. The ITU, in document ITU-T Y.2060, defined IoT as:
“ a global infrastructure for the information society, enabling advanced services by interconnecting (physical and virtual) things based on existing and evolving interoperable information and communication technologies.”
Which basically means, that it is a network of things (devices, sensors, people, etc) which can collect, share, use and act on data from their environment. This can include things like an outdoor thermometer, a smart fridge, a smart toilet seat, an auto-driving-cars or even a smart factory.
IoT Landscape and areas of application
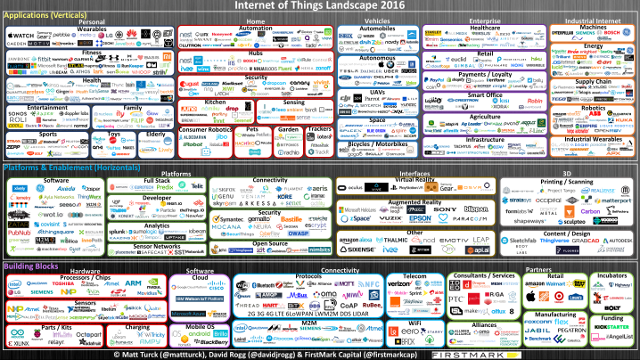
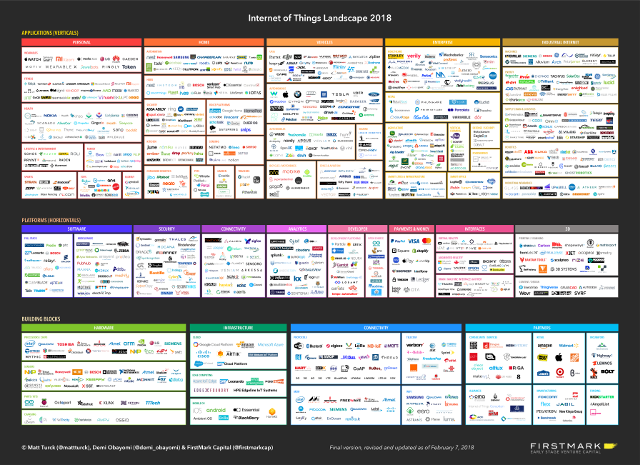
Some of the best articles that describe and analyze the IoT landscape are by Matt Turck. He was one of the first to study this topic and his first analysis dates back to 2016 . The latest version is from the beginning of 2018.
As part of his work, he also created these poster size slides that group companies into vertical and horizontal markets. The first are focused on satisfying the needs of a particular industry or niche, while the latter focuses on satisfying need across industries.
The version from beginning of 2018 saw an increase of almost 35% in the amount of logos on the chart, from 721 to 971. 96 companies were removed from the chart and 346 new companies were added. A small number of typically very large companies have their name in several categories.
If you take a closer look at the full size diagrams of the landscape from 2016 and landscape of 2018, you may recognize many of the companies on the chart and especially the different areas on it:
- Personal (wearables, fitness, health, lifestyle, elderly care, …)
- Home (automation, hub, security, kitchen, pets, …)
- Vehicles (UAVs, autonomous, marine, bicycles, …)
- Enterprise (healthcare, retail, agriculture, smart cities, smart office, …)
- Industrial Internet (machines, energy, supply chain and logistics, robotics, …)
- Analytics and many more
The landscape is so big that it is very hard to keep track of all of the moving parts.
IoT Security
The events of the last couple of months and years have shown that Security is and will continue to be one of the main issues (or handicaps) in the Internet of Things. There have been many incidents, for example: the botnet Mirai in September 2016, Cloud Pet was hacked and held for ransom in February 2017, smart locks by Lockstate were broken by a firmware update in March; almost 8000 Telnet credentials to IoT devices were exposed in August 2018, and the list just goes on and on.
Given focus on the “time-to-market” and keeping prices low, security continues to be an afterthought. In many cases the companies and developers are missing the framework, the know-how or the time to implement security into their solutions.
The proliferation of many IoT Cloud Infrastructure offerings, for example from Amazon AWS, Microsoft Azure or Libelium, to mention a few; will raise the bar in the future, but until then we will still see multiple incidents.
What makes IoT Security so complex?
The Internet of Things, is complex by nature. It involves multiple layers and components, and in most cases using different technologies, working with each other. If we take a look at a reference architecture, we can identify:
- Devices / Sensors / Things
- Communication protocols
- Gateways (optional)
- Networking
- Data collection
- Visualization / Action / Applications
This creates an attack surface that can be split into 4 categories:
- Device security vulnerabilities
- Firmware based vulnerabilities
- Mobile, Web and Infrastructure, and Network security issues
- Radio communication based vulnerabilities
Here we have grouped what can be considered as the traditional IT security scope into point 3. The others are not new but claim more relevance in this context.
From a security point of view, it is important to always consider the big picture (overall architecture and design), as well as to pay attention to details (low level design and implementation). Especially in highly complex environments.
There is no current industry standard for IoT Security, but there are multiple organizations and many people working on this, for example the OWASP Internet of Things (IoT Project), the IoT Security Foundation, GSMA IoT Security Guidelines, and much academic work.
When should security be taken into account in an IoT project? The answer, as usual: the sooner, the better.
Different studies show that there is a significant better Return on Investment (ROI) for addressing security in the design phase, compared to after implementation or short before go-live. The costs can be up to 30 times higher, when done at the end.
Kickstart a career in IoT Security
Adopting a security career path has multiple incentives, from which the following can be highlighted:
- Cybersecurity professionals enjoy high wages, that can go somewhere between 50K and 120K USD a year with a median in Europe of around 80K Euros. There are many publications that confirm this trend, like this article from CSO Online (7 of the highest paying jobs in cybersecurity in 2018), or this one from the The Robert Walters 2018 Salary Survey.
- There is a very high demand for security professionals, and for the foreseeable future there will not be enough qualified professionals to fulfill this demand. Currently, there are just too many threats and too few professionals. There are multiples studies by ISACA and many other institutions that highlight this.
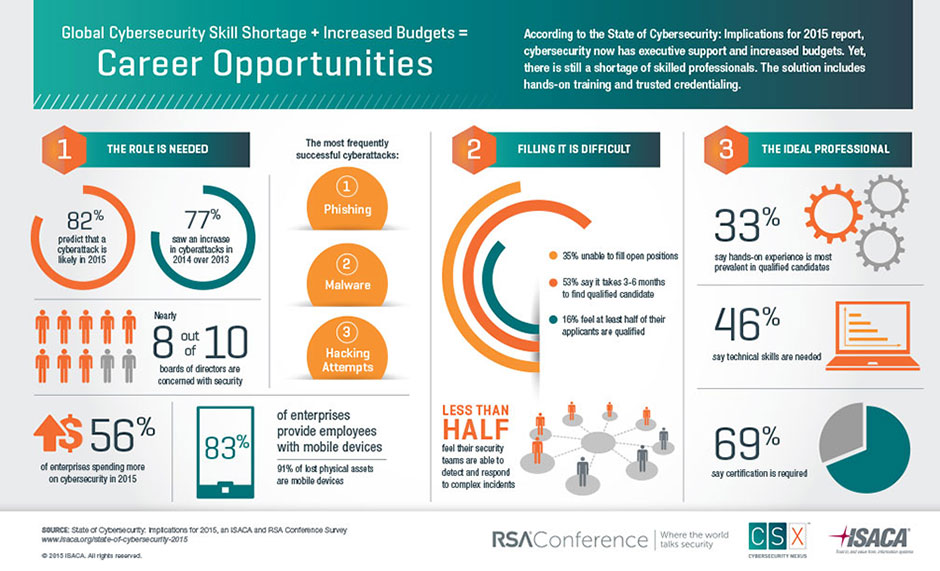
ISACA – RSA Conference – Career opportunities in Cybersecurity
- There is a shortage of skilled cybersecurity professionals. For example, the Computer Business Review cites a study by ISC2 that says that Europe alone will need 350.000 cybersecurity professionals by 2022.
- Constant growth and learning: for those, who enjoy constantly learning new technologies and concepts, it is definitely the right path. The constant change and evolution assures that the job will never get boring.
- Getting paid to “hack” can be in many cases compared to getting payed to do your hobby. Of course, there are better days than others, but in general most security practitioners feel this way.
What is needed to start a career in security?
There are many great articles on how to start a career in infosec or cyber security. But it comes down to a triad of education, experience and training.
- Education: with a good education you build the fundamental knowledge needed for your career path and one of the most important skills: you learn how to learn.Self-study is an important skill, but it is hard and not for everyone. You can look for training programs for certifications or formal programs specialized in computer science, engineering or even electronics. When studying, make sure to include operating systems, networks, some databases and even programming.
- Experience: everything you do adds up to experience. From playing with a Raspberry Pi, to hacking vulnerable boxes or applications. Your experiences help fine-tune your abilities and the results you obtain.Get in touch with communities or local chapters of known organizations like: OWASP, ISC2 or CEH. Even a maker group will provide you with valuable experience with electronics and people, that will come in handy.
- Training / Certifications: these get you a foot in the door or even help you obtain an interview for a new job. They prove to your actual and future employers that you have competences in different fields, i.e. threats and vulnerability management or even pentesting skills.CompTIA Security+ is a good starting point, from which you can follow different career paths: management, infosec or even more technical implementation or hands on. ISECOMs OPST, OPSA are very complete and do not have requirements of experience like ISC2s CISSP or ISACAs CISM or CISA. On the technical side the OSCP is known to be one of the hardest to obtain.Take a look at our article comparing trainings and conference to help you pick we is the best for you at this moment.
You can find lots of information on this topic, but we recommend Fabio Baroni’s article “Cracking the infosec interview for fun and profit – how not to suck and get $$ hired $$“, or Ron Woerner’s article on Peerlyst: ”Breaking into Security Careers – 2018”.
Why should you attend IoT Security Trainings?
There are many reasons to attend IoT Security Trainings or bootcamps. Here are five we consider the most relevant:
IoT is complex and the security aspects involve multiple layers and components. It is important to have the complete overview before diving into just some of the details.
Learning about IoT requires a lot of time and there is lots of material to cover: Firmware, Embedded Devices, Serial communication protocols, Software Defined Radio, Bluetooth Low Energy (BLE), ZigBee and lots more!
This takes a lot of time and energy. A training or bootcamp can give you a kickstart so that you land on your feet and running; with the know-how, techniques, tactics, and tools; as well as the hands-on experience.
As we mentioned above, to get hired as a security professional or to progress in this career path, you need a mix of: experience, education, and certifications. It takes all three to not only land the job, but also be successful in it. The SevenShift IoT Security Bootcamps provide you all three, including a certificate of completion.
Completing a good training will set you in right path to find 0-days, security vulnerabilities, claim CVEs, win Capture the Flag (CTF) contests or collect bounties on platforms like HackerOne or Synack. It is possible to do this without it, but a training helps you reach this level faster.
If you are a curious person, who likes to understand how things or different technologies work, then a good training is the best environment for you. Each module should start by laying down the theory and the basics of how these things work. Once you have understood them, hacking them is a lot easier. Hacking is about knowledge and not poking things in the dark to see if the break.
SevenShifts IoT Security Trainings
SevenShift has developed a series of IoT security trainings and workshops to fit any profile, from managers to pentesters.
- IoT Security for Managers: everything what a Manager should know to make an IoT project secure.
- IoT Security Bootcamp: 3 days Hands-on. Learning-by-Hacking. For those who want to understand the security and technical details to it. A hacker course for non-hackers.
With your registration to the bootcamp, you will receive a free IoT Hacking Kit (hardware with a value of +300 Euros), which contains the tools and some vulnerable devices, so that you can continue sharpening your skills or hack devices after the event.
Our trainings take place at least twice a year, please check the training page to find the exact dates and locations.
About the Trainer
The trainer is an actual security practitioner, not just a trainer. Pablo has 15+ years of experience in IT and Cybersecurity. He has tested dozens of devices and IoT ecosystems in the last 2-3 years. This experience allows him to provide insights of real world pentesting and consulting. He will talk about the most common findings, how to identify them and exploit them. Most importantly he will share the tools and tactics used in his projects.