Hooray, we made it!
The IoT Security Bootcamp in Cologne in November 2018 was a success!
The class flow was pretty good, almost all of the exercises and demos worked and most important of all we all learned a lot: students, staff and the trainer.
I must say: this was our biggest endeavor in 2018. We started with the planning and preparations more than a year in advance and it kept us really busy until a week after we finished the class.
After having done it once, I must express my deepest respect to the organizations and trainers that have been doing this for long time. First of all, you have set a high bar. Second, it is a titanic amount of work, but really rewarding. Seeing how students can actually take away a good experience, some knowledge and tricks that they can apply on their daily work.
I’ve had the pleasure of keeping in touch with our first batch of students and I’m happy to report that they have all gone out to apply what they learned in class.
In the following sections I will describe our class, talk about the feedback we received and the changes that we have implemented for our Bootcamp in 2019. As well as announcing the next dates you can book your very own IoT Security Bootcamp.
Day One: Intro and firmware
We had a soft start on day one, setting up the lab (installing the VM with all the tools) and since we had a small group, we did a short round of introductions.
The next couple of hours, we did a introduction to IoT Security to get everybody on the same page: what is IoT, the attack surface (device, firmware, networks and gateways, apps and backend), components involved, some discussions on data and privacy, and so on.
After the lunch break, we went over different pentesting methodologies, like OWASP, OSSSTM, Kali and the IoT Pentesting Methodology. After we all had a high level idea of what we were going to do, we dove into firmware hacking.
This module is really fun, unpacking, reverse engineering and emulating Linux based firmware. We use tools like hexdump, dd and binwalk, for the basics and then work with other open source tools and scripts, like qemu, FAT and firmadyne to do the heavy lifting.
I tend to stay away from teaching how to dissect non-Linux binaries, ARM assembly and reversing, because there are people who are really better at doing and teaching that than me, for example Azeria.
Day Two: Web Apps, Network security and Android
This day was really intense, because we have lots of material to go through. Based on the feedback from this group, we decided to remove this content from the IoT Security Bootcamp. It will be taught as an individual class or as a 5-day training (these can requested as private classes).
For the WebApps, we talked about OWASP Mobile: the methodology, the top 10, requirements and the testing guide. For the hands-on component we work with some vulnerable web applications and a proxy.
Network security was focused on following the pentest methodologies, by performed scans and attacking a vulnerable IoT device. One of the important lessons when hacking IoT is that you have to throttle the power of your tools to match the CPU of the device: you can’t perform 500 login attempts per second on a small arm based device. It just can’t cope with it.
Mobile is a important component in IoT, most of the device have mobile App to help control them. We worked with Android for the hand-on component of this class. Especially because of the requirement of the testing environment.
Day Three: BLE, Hardware Hacking and SDR
For all these modules, we played with lots of the components of the IoT Security Hacking Kit. For Bluetooth Low Energy or BLE, we attacked a BLE light bulb with sniffing, MiTM attacks and the Linux Bluetooth stack. The poor bulb did not stand a chance.
For the hardware hacking module, we put on our maker hats: used the arduino, jumper cables, the USB to serial (UART, JTAG, IC2, etc) adapters, and the rest of the electronics included in the kit; to learn how to extract information and gain control of the IoT devices on a hardware level. For one of the last exercises, we connect to a micro-controller via a debugging interface to bypass authentication on a serial interface.
We closed the day working with Software Defined Radio (SDR). First learning the concepts and then putting them to work to capture, reverse engineer and perform attacks on the non-regulated ISM bands, like 433 MHz.
Feedback, next classes and improvements
We got very positive feedback from our group:
“Great workshop, very interesting topics, cool location and really awesome hands-on exercises! Pablo is great at explaining things and he took the time to understand individual questions.”
“Not working as a security expert myself but rather being in device development, I still found the Workshop extremely useful and interesting to get a quick but extensive overview over the IoT security Topic. Especially the Hands on Trainings have greatly improved the learning Efficiency and the Impression I got from the Workshop. “
“Looking forward for more workshops!
Very experienced instructor, very good preparation and good presentation!”
Based on the experience and the feedback they provided, we decided to slim down the content of our 3 day class. For 2019, we will focus on the parts that are really IoT specific and do even mode hands-ons exercises on these modules: firmware, BLE, hardware hacking and SDR or wireless hacking. The other modules will be available on a 5-day class or dedicated trainings on these topics.
For 2019 we already have dates that are open for registration and are working on getting a couple more:
- IoT Manager Training 2019-05-13 – Cologne
- IoT Security Bootcamp, 2019-05-14 – 2019-05-16 – Cologne
- IoT Manager Training, 2019-11-25 – Cologne
- IoT Security Bootcamp, 2019-11-26 – 2019-11-28 – Cologne
So remember to book on time to reserve your seat and take advantage of the early bird pricing.






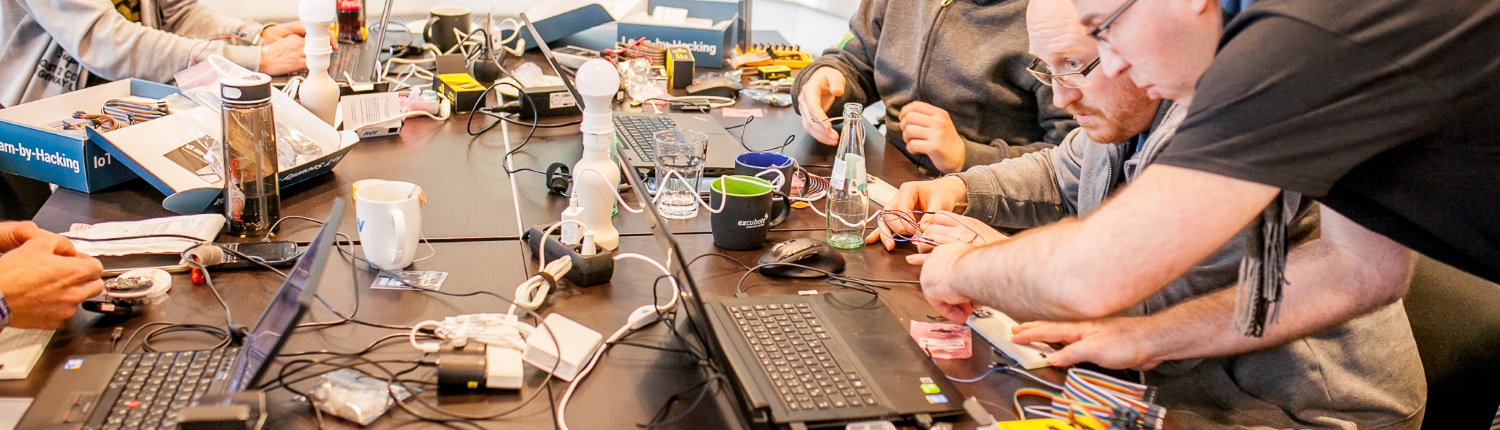




 Photo by Braden Collum on Unsplash
Photo by Braden Collum on Unsplash